Towercell - Multi-Level Safety Protection
Fully protect system security from the bottom of the hardware to the cloud
Related Background
With the continuous integration of information technology, the Internet and the automobile industry, automotive network connectivity and intelligence have become an inevitable trend in the development of the automotive industry. As of August 2021, the number of connected car users in China has exceeded 50 million. Most modern vehicles have more than 100 ECUs, and these ECUs are running more than 100 million lines of code. For a networked car, from an isolated and closed network environment to a complex and diverse Internet environment, many functions based on the closed network environment will undergo disruptive changes in design, and network information security will become the biggest security challenge. Under the complex automotive architecture, the threats faced by the in-vehicle system may be multi-layered, from firmware flushing at the hardware level, to ROOT permission theft at the system level, to APP vulnerability and sensitive information theft at the application level, and so on. Therefore, to ensure the overall security of IVI, it is necessary to establish a multi-layered three-dimensional defense strategy.
TowerCell
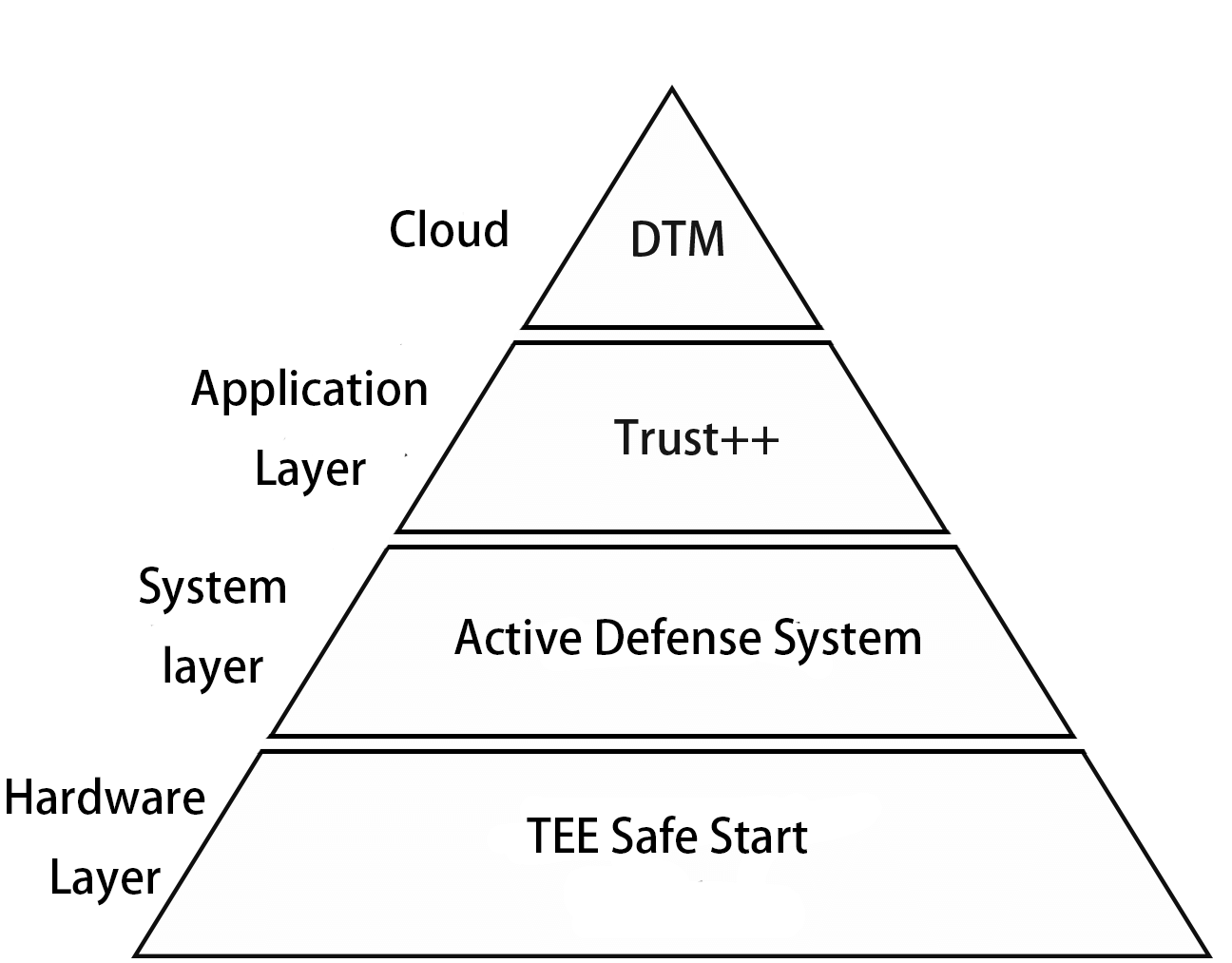
Any security hole in the framework could result in an attacker taking full control of the device.The TowerCell platform provides multi-level protection policies to ensure that data at all levels and phases cannot be tampered with to ensure system security.By formulating a complete set of three-dimensional security policies from the hardware layer to the application layer, from the terminal to the cloud to ensure the overall security of the system from the start-up stage to the operation process.
Hardware layer:
Secure start-up inspection equipment completeness and establishment of a trusted execution environment
System layer:
Active defense system detects kernel status in real time to prevent problems before they occur
The vulnerability risk associated with increasing code volume can also spike significantly. However, for an operating system such as Android with over 10 million lines of code. It is certainly not realistic to completely eliminate the creation of vulnerabilities, and not all vulnerabilities create intuitive harm and loss to users. Rather, the existence of this vulnerability may be exploited by third parties to tamper with key kernel data, obtain more advanced privileges, and then attack system components to obtain user access. Therefore, the most important thing to do to prevent vulnerabilities is to make sure that the most important thing is to have the ability to monitor and manage the critical data nodes of the kernel.
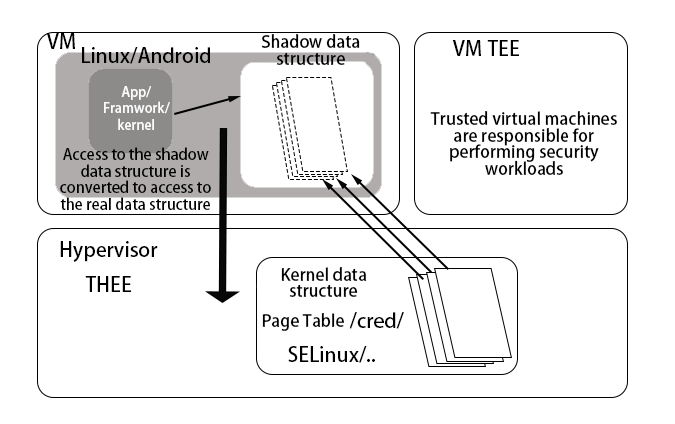
TowerCell will run our own Hypervisor THEE in EL2 mode (Hypervisor) to monitor and manage the kernel by THEE.
Application layer
Trust++ Open Trusted Execution Environment Security Capabilities to Protect Massive Number of Applications
The main problem for application protection is that it is not possible to effectively secure this part of the business in the process of carrying out the core business. In most scenarios, this part of the core business is exposed or run in a complex system environment with simple encryption.
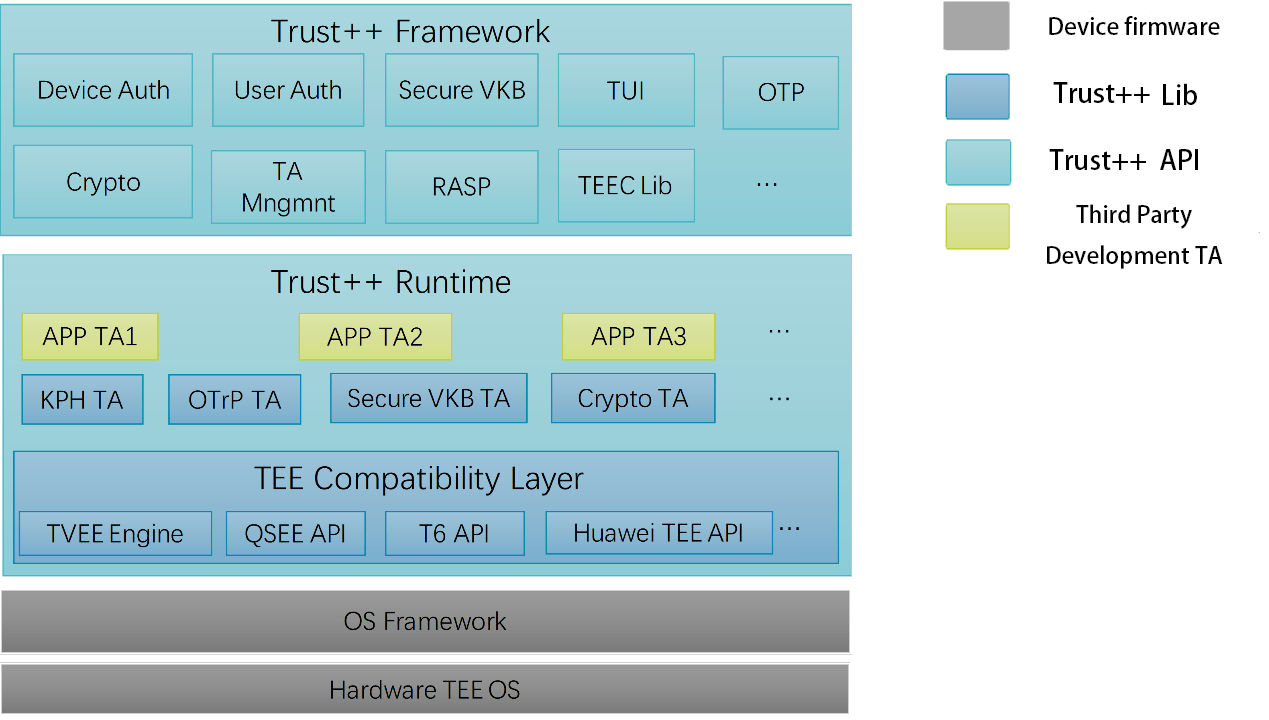
At the application layer, TowerCell uses Trust++, a Trusted Execution Environment (TEE)-based application security solution for application vendors. It is mainly used to solve the code, data and business security problems of applications in smart devices, and provide a secure operating environment for users' sensitive business.
Security
Trust++ leverages the most secure mechanisms available in the device (including hardware and software mechanisms such as ARM TrustZone, virtualization, Intel SGX, etc.). virtualization, Intel SGX, etc.), combined with the original native encryption execution engine, compiler security, code protection, and The application is secure by leveraging the most secure mechanisms available in the device (including hardware and software mechanisms such as ARM TrustZone, virtualization, Intel SGX, etc.).
Cloud:
DTM platform real-time monitoring, timely response
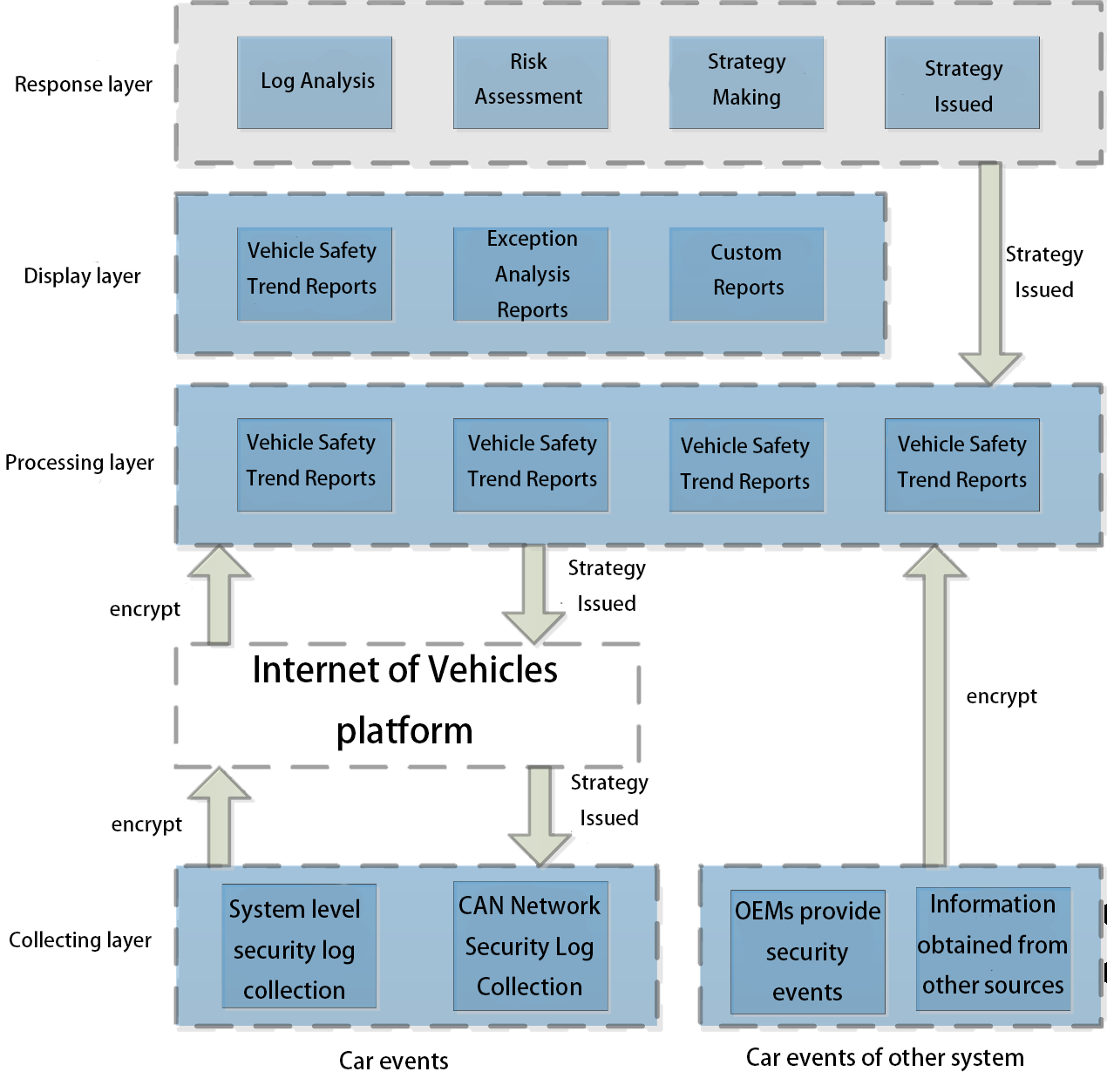
We can use different protection strategies to minimize the creation of vulnerabilities or reduce the damage caused by vulnerabilities. But for a vulnerability that has been created, we still need a good strategy to fix it. For operations and maintenance personnel, to be able to timely collect information related to the vulnerability generated in the device terminal. to be able to timely develop a good security policy issued in a timely manner.
At the application layer, TowerCell uses Trust++ to secure applications. The Trust++ product is an application security solution for application vendors based on the Trusted Execution Environment TEE. It is mainly used to solve the code, data and business security problems of applications in smart devices, and provide a secure operating environment for users' sensitive business.
Positioning problems
Visual threat presentation locates a terminal, a process and a path. The log information uploaded from the device side is classified and processed to create reports for maintenance personnel. Allow maintenance personnel to easily analyze the source of vulnerabilities
Application Cases
PKI Application Scenarios
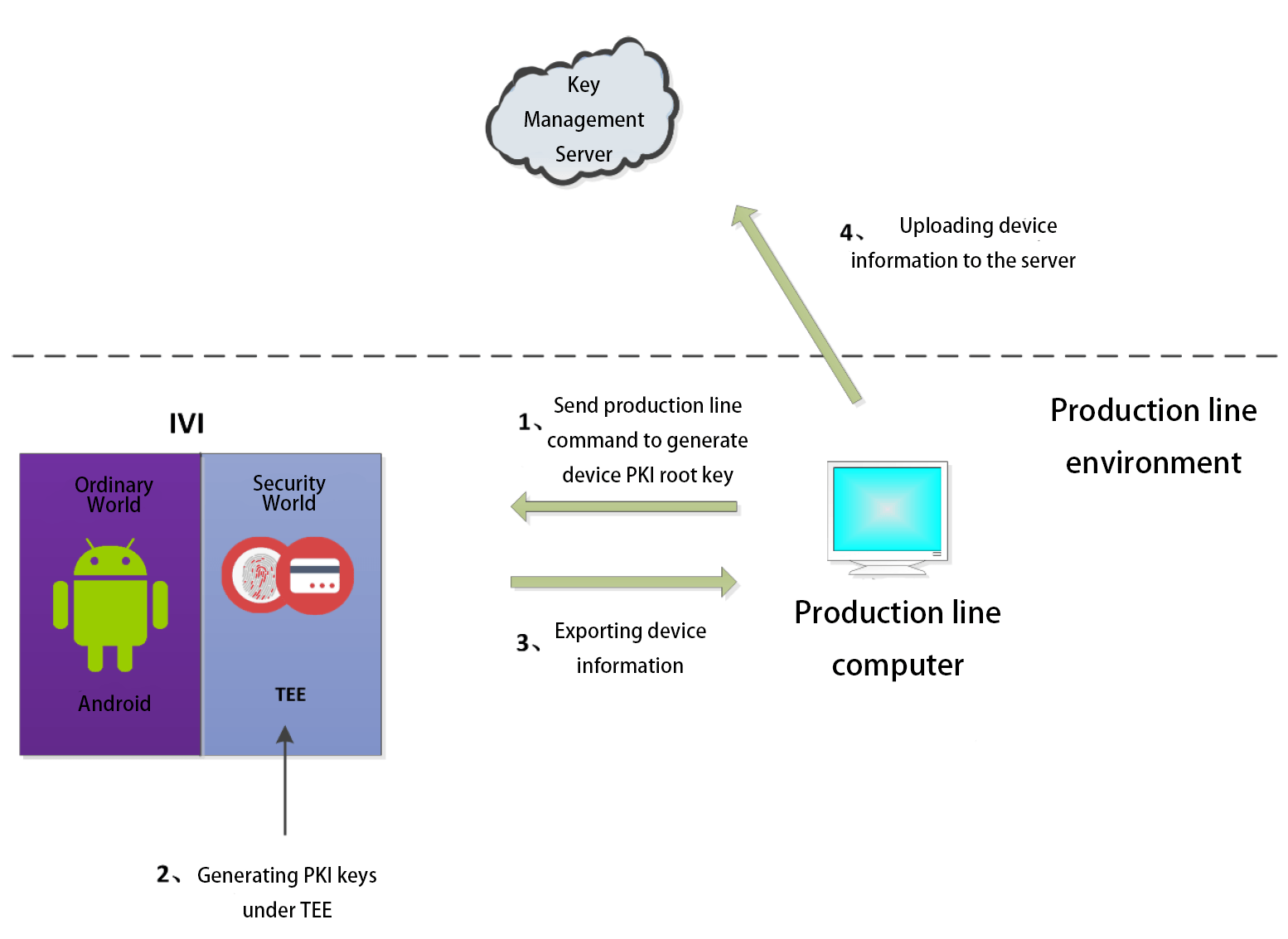
Trusted root generation process
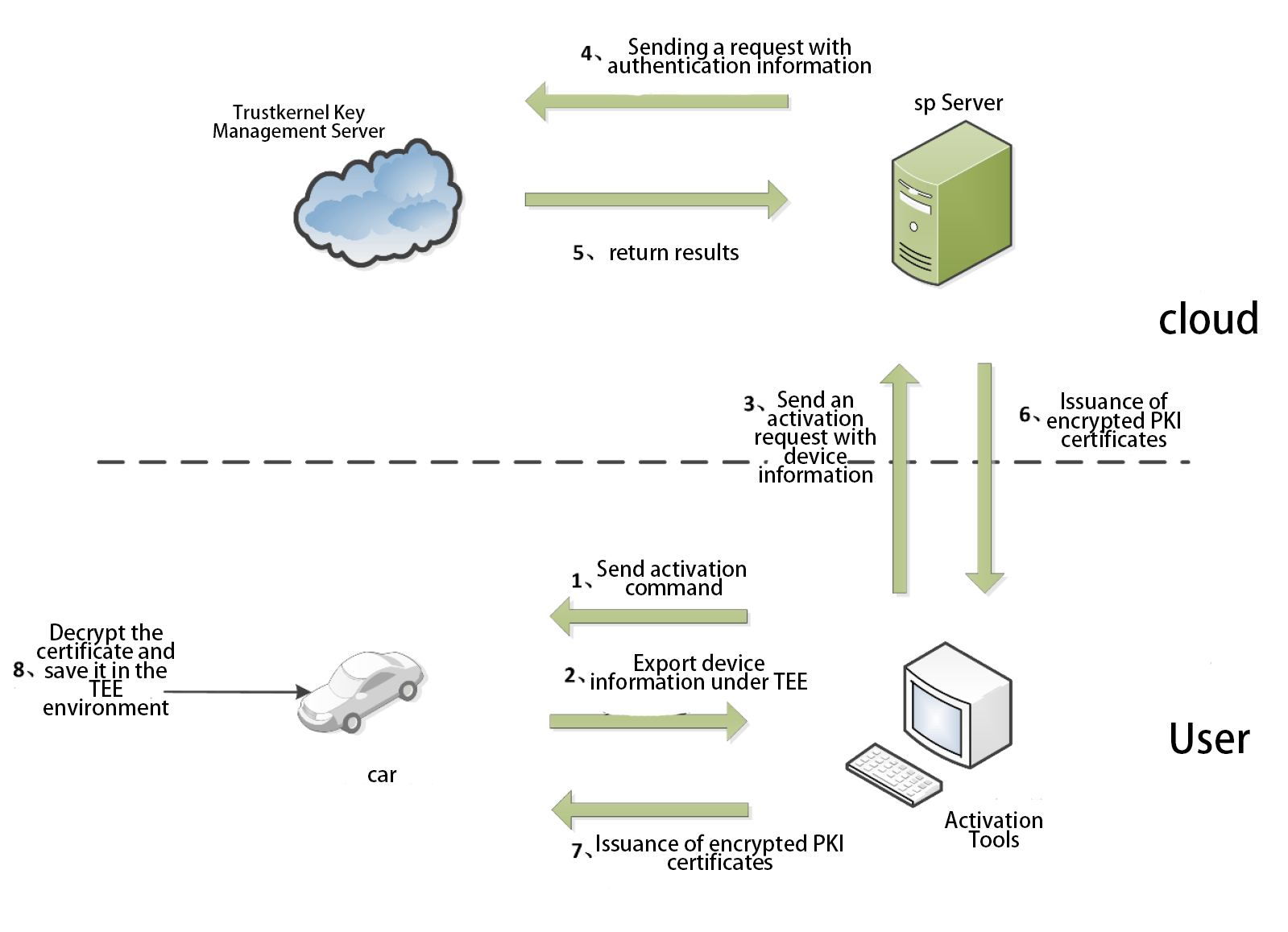
PKI activation process
In the process of authentication on the device side and in the cloud, it is a more effective practice to establish a PKI system. However, for PKI, if the absolute security of the activation process, key certificate storage, etc. cannot be guaranteed, then even if PKI is used, it cannot achieve the expected security protection. The traditional PKI system implants a set of keys into the device at the production line stage as the basis for subsequent PKI activation. TowerCell generates a pair of root keys for each device under TEE at the production line stage. The private key is strictly held by the TKCORE OS of the device and will not be disclosed in any form. The generated public key will be exported and uploaded to Trustkernel's key management server for unified management. During the device activation phase, it is important to ensure the security of the root key usage environment. TowerCell provides a secure activation environment for the device. The device will sign and upload the authentication information to the manufacturer's PKI server in the TEE environment, and after receiving the authentication information, the PKI server will After receiving the verification information, the PKI server sends the data to Trustkernel's key management server for verification. After receiving the verification information, the PKI server sends the data to Trustkernel's key management server for verification. With the verification result returned by Trustkernel's key management server, the PKI server decides whether to issue the PKI certificate (encryption issuance). When the device receives the encrypted PKI certificate, it will decrypt the certificate under TEE, and the PKI certificate will be stored under TEE and can only be used under TEE. The PKI certificate is stored in the TEE and can only be used under the TEE, effectively ensuring that the certificate will not be leaked. At the same time, TowerCell can control the frequency of device access to the cloud. When a single device is compromised by a malicious attacker The device may send a large amount of information to the cloud through this device to occupy the limited resources of the cloud. In this case, the TowerCell can be used to limit the frequency of access to the device to stop the damage caused by this big data flush.
Usage scenarios for Trust++
Trust++ provides rich security application scenarios, and users can use the SDK to call the relevant interface to use security features using the target language (such as JAVA).

Identity verification
Developers can call the SDK's interface to send data to a specified server to perform authentication work

Feature-rich encryption and decryption libraries
Feature-rich encryption and decryption library: Trust++ provides a powerful feature library that supports basically all encryption and decryption algorithms on the market.

Secure Storage
Trust++ builds secure runtime and storage environments by leveraging the most secure mechanisms that can be used in the device. Developers can use the interface provided by Trust++ for secure storage to securing private data such as keys.

Trustworthy UI
Trust++ provides a set of call interfaces for security UI. Users can easily design their own security UI by choosing the style and layout of their UI through the relevant interface
 沪公网安备31011202008280号
沪公网安备31011202008280号